

How Not to Get Hacked in Crypto
Crypto security has never been more critical. With SIM swaps, phishing scams, and wallet exploits reaching new heights, 2025 is shaping up to be a year where robust security isn’t just an option—it’s a necessity. In this guide, we break down the latest threats, share real-life examples, and offer practical tips to help you safeguard your digital assets in this volatile space.
Overview of Crypto Security in 2025
The digital asset world is evolving at a breakneck pace, bringing with it both incredible opportunities and significant risks. In 2025, crypto adoption is at an all-time high, driven by mainstream financial institutions, improved blockchain technology, and a growing global interest in decentralized finance (DeFi) and Web3. However, as the crypto ecosystem expands, so do the tactics and sophistication of cybercriminals.
From SIM swaps and phishing scams to smart contract exploits and wallet vulnerabilities, hackers are constantly finding new ways to steal funds and sensitive information. In fact, the global cost of crypto-related cybercrime is expected to surpass billions of dollars this year. According to blockchain security firm Chainalysis, crypto-related attacks in 2024 already resulted in losses exceeding $3 billion, and the trend is expected to continue in 2025 as new attack vectors emerge.
Understanding the Threat Landscape
In 2025, the crypto threat landscape is evolving faster than ever. As more people enter the world of digital assets, hackers are developing increasingly sophisticated methods to exploit vulnerabilities and steal funds. recent example is African Magnate Mohammed Dewji Falls Victim to Latest Crypto Hack: Unmasking the $TANZANIA Scam
Staying ahead of these threats requires understanding how they work and what you can do to protect yourself. Let’s break down the major types of attacks you need to watch out for.
Rising Incidence of SIM Swaps
SIM swap attacks are skyrocketing globally, with criminals targeting mobile phone numbers to take control of victims’ digital identities. In these attacks, hackers contact your mobile service provider, impersonate you, and convince them to transfer your phone number to a new SIM card. Once they have your phone number, they intercept two-factor authentication (2FA) codes and gain access to your crypto accounts, email, and even social media profiles.
Why SIM Swaps Are So Dangerous:
- Direct Access to Crypto Accounts: Many crypto platforms use SMS-based 2FA for account recovery or transaction verification. If a hacker controls your phone number, they can bypass this security layer.
- Identity Theft: Beyond crypto, SIM swap victims often experience identity theft, where attackers access email accounts, reset passwords, and wreak havoc on personal finances.
- Immediate and Irreversible Losses: Once funds are transferred out of a crypto wallet, they’re virtually impossible to recover.
In 2024, a high-profile SIM swap attack resulted in the theft of over $4 million in crypto from a prominent trader. Despite using multiple layers of security, his reliance on SMS-based 2FA left him vulnerable. The attack lasted less than an hour, but it wiped out years of savings.
How to Protect Yourself from SIM Swaps:
- Avoid SMS-Based 2FA: Use authenticator apps like Google Authenticator or Authy for stronger protection.
- Enable Account PINs with Your Carrier: Many mobile providers offer account-level PINs that must be provided before making changes to your phone number.
- Consider a Dedicated Device for 2FA: Using a separate device for authentication can significantly reduce your risk.
Phishing Scams in the Crypto Space
Phishing attacks remain the most common and effective way for hackers to steal your crypto. Unlike early phishing attempts that were easy to spot, today’s scams are highly sophisticated and designed to mimic trusted sources with frightening accuracy. These scams often arrive via email, SMS, or social media and trick users into revealing sensitive information or downloading malware.
Common Phishing Techniques:
- Impersonating Media Outlets or Influencers:
One of the most dangerous phishing tactics involves fake invitations from “reputable” sources like the BBC or Bloomberg. Victims receive a link to join a “Zoom interview,” which is actually a phishing site designed to harvest their wallet credentials.- In early 2025, several crypto influencers lost access to their wallets after clicking a link in a fake BBC invitation that claimed to offer media coverage for their projects.
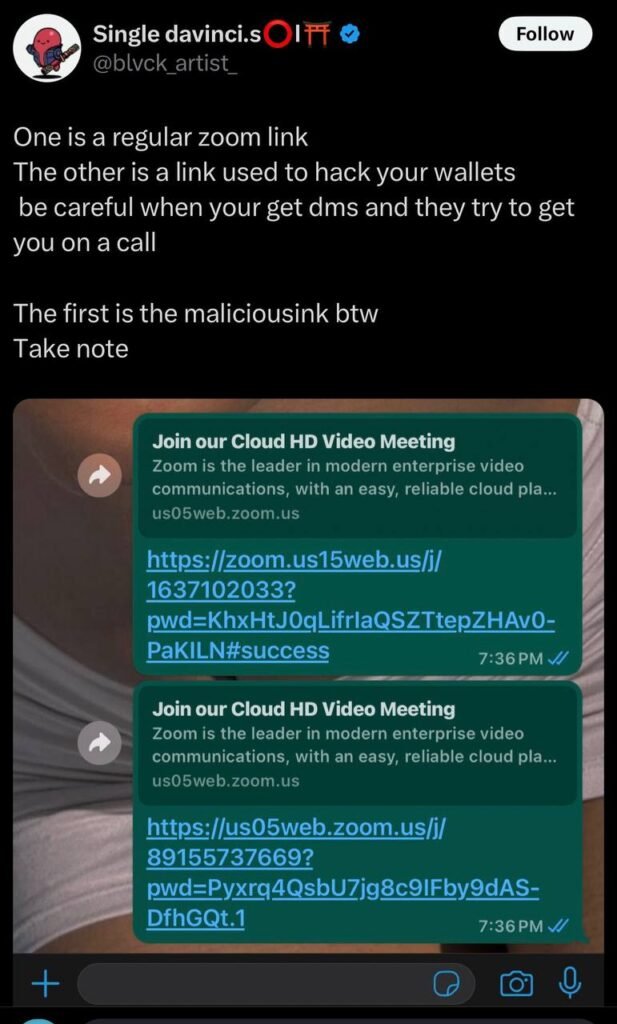
- Social Media Account Takeovers:
Some phishing scams target crypto projects users have previously authorized to access their X (formerly Twitter) accounts. Hackers leverage these old permissions to post malicious links from legitimate accounts, making the attack seem authentic.

Fake Airdrop or Token Offers:
Hackers often lure victims with promises of free tokens or exclusive airdrops. Once users connect their wallets to claim the “reward,” their funds are drained.
How to Stay Safe from Phishing Attacks:
- Double-Check URLs: Always verify the domain before entering sensitive information. Bookmark important crypto sites to avoid fake ones.
- Enable Anti-Phishing Features: Use wallet services that offer anti-phishing tools, like MetaMask’s warning system, to block malicious sites.
- Stay Skeptical: If something feels too good to be true—like free money—it probably is.
Wallet Exploits and Vulnerabilities
Wallet security is the cornerstone of protecting your crypto assets. While hardware wallets (cold wallets) are generally considered the safest option, they aren’t completely immune to threats. Meanwhile, hot wallets, which are connected to the internet, are prime targets for hackers.
Types of Wallet Vulnerabilities:
- Hot Wallet Hacks:
Hot wallets are essential for day-to-day crypto transactions, but their constant internet connection makes them vulnerable to malware and phishing. Hackers can exploit weaknesses in browser extensions or malicious smart contracts to drain funds. - Cold Wallet Mismanagement:
Cold wallets like Ledger or Trezor are safer because they aren’t connected to the internet. However, human error—like losing recovery phrases or storing them digitally—can lead to catastrophic losses.- Example: In 2023, a user lost access to $500,000 in crypto after accidentally sharing his recovery phrase in a screenshot uploaded to a cloud service.
- Smart Contract Bugs:
DeFi wallets connected to smart contracts can expose you to vulnerabilities in the code. If the smart contract is poorly written or not audited, hackers can exploit it to drain funds.
How to Fortify Your Wallet Security:
- Use Multi-Signature Wallets: Multi-sig wallets require multiple approvals before transactions are executed, adding an extra layer of security.
- Secure Your Recovery Phrases: Write them down on paper and store them in multiple secure locations. Never save them digitally.
- Regularly Update Wallet Software: Ensure your wallet firmware is up to date to patch security vulnerabilities.
Why Understanding These Threats Matters
The crypto space is an exciting frontier, but it’s also a highly targeted one. Being aware of these common attack methods and knowing how to defend against them can mean the difference between keeping your funds safe and becoming the next cautionary tale. In the following sections, we’ll dive deeper into the tools and strategies you can use to create a bulletproof security plan for your crypto assets in 2025.
Best Practices for Protecting Your Crypto Assets
In the fast-paced world of cryptocurrency, the stakes are high. The evolving threat landscape calls for proactive security measures to safeguard your digital assets. Whether you’re a seasoned investor or just entering the crypto space, implementing best practices is crucial to minimizing risk. This section provides a comprehensive guide to fortifying your crypto security.
Strengthening Authentication Methods
- Multi-Factor Authentication (MFA) is Non-Negotiable
Relying solely on passwords is a recipe for disaster in 2025’s crypto environment. Hackers have become adept at stealing or guessing passwords, making MFA an essential layer of defense. However, not all MFA methods are created equal. - While SMS-based two-factor authentication (2FA) is still widely used, it’s increasingly vulnerable to SIM swap attacks. Instead, opt for an authenticator app like Google Authenticator, Authy, or Yubico’s security keys for more robust protection. These apps generate time-based one-time passwords (TOTP) that are far more secure than SMS codes.
- Password Management Matters
Creating strong, unique passwords for every crypto-related account is critical. A password like “Crypto123” simply won’t cut it. Instead, use a combination of uppercase and lowercase letters, numbers, and special characters. A reputable password manager like 1Password or Bitwarden can generate and store complex passwords for you, ensuring that each account remains unique and secure without needing to memorize them all.
- Tip: Never reuse passwords, especially for your email and crypto exchange accounts. If a hacker gains access to your email, they can reset your crypto account passwords and drain your funds.
Securing Your Mobile Devices Against SIM Swaps
- SIM swap attacks are becoming a go-to strategy for hackers targeting crypto users. These attacks involve fraudulently transferring your phone number to a new SIM card, allowing attackers to intercept 2FA codes and gain access to your accounts. The consequences can be devastating.
- Work with Your Mobile Provider to Add Extra Security
Contact your carrier and request additional security measures. Most providers offer options to set up a unique PIN or password on your account, which must be provided before any changes can be made. Some carriers also offer “port-freezing” services, which prevent your number from being transferred to another SIM card without your express permission. - Stay Alert for Suspicious Activity
Be vigilant. One of the earliest signs of a SIM swap in progress is the sudden loss of mobile service. If your phone shows “No Service” unexpectedly and you’re not in a dead zone, contact your carrier immediately. Acting quickly can prevent hackers from completing the attack.
Recognizing and Avoiding Phishing Scams
- Phishing scams are among the most effective tools in a hacker’s arsenal. They come in many forms—emails, text messages, social media posts, and even fake websites—all designed to trick you into giving up sensitive information.
- Identify Red Flags and Verify Sources
Phishing attempts often mimic legitimate organizations, using logos and language that appear authentic. Always double-check email addresses and URLs. Hackers will often use addresses that look similar to trusted sources but with slight alterations, such as replacing an “o” with a zero or adding an extra character. - Practical Example: Imagine receiving an email from “support@binance-safety.com” warning you of suspicious activity and urging you to reset your password. If you click the link and enter your credentials, you’ve just handed them over to hackers.
- Avoid Clicking on Unverified Links
Hover over links in emails to reveal the full URL before clicking. If it looks suspicious, don’t take the risk. Instead, bookmark the official websites of your crypto platforms and access them directly. This simple habit can save you from falling into a phishing trap.
Enhancing Wallet Security
- Your wallet is your most critical line of defense in the crypto space. The security of your funds depends on how you manage your wallet.
- Prioritize Cold Storage for Long-Term Holdings
Hot wallets—those connected to the internet—are convenient for frequent transactions but are inherently riskier. For significant holdings, cold storage is the way to go. Hardware wallets like Ledger and Trezor offer offline storage solutions that are virtually immune to hacking. - Stay Up-to-Date
Wallet software is continuously updated to patch security vulnerabilities and improve functionality. Regularly check for updates and apply them immediately. Ignoring updates could leave you exposed to known exploits. - Backup and Protect Your Keys
Your private keys and recovery phrases are the only way to access your funds if something happens to your wallet. Keep secure, offline backups in multiple locations, such as a fireproof safe or a secure storage box. Never store your recovery phrase in plain text on your computer or phone, as these can be easily compromised.
The Bottom Line
Protecting your crypto assets requires a multi-layered approach. By strengthening your authentication methods, securing your devices, staying vigilant against phishing scams, and prioritizing wallet security, you can significantly reduce your risk. Remember, in crypto, you are your own bank—and with that comes the responsibility to secure your digital assets diligently.
Essential Tools and Resources for Securing Your Crypto Assets
Recommended Hardware Wallets and Security Software
When it comes to protecting your crypto assets, hardware wallets and security software are your first line of defense. They offer robust solutions for minimizing the risks associated with online threats and provide peace of mind for long-term crypto holders.
Hardware Wallets: The Gold Standard for Cold Storage
Hardware wallets are physical devices that store your private keys offline, making them immune to online attacks like phishing, malware, and keyloggers. Unlike software wallets connected to the internet (hot wallets), hardware wallets keep your assets secure even if your computer is compromised.
Ledger: Ledger wallets, such as the Ledger Nano X and Nano S Plus, are highly regarded for their advanced security features and broad support for different cryptocurrencies. They offer Bluetooth connectivity for convenience and integrate with popular crypto management apps like Ledger Live.
Trezor: Known for its user-friendly interface and high security, Trezor is another trusted name in the hardware wallet market. Its flagship models—Trezor One and Trezor Model T—are widely used by both beginners and seasoned investors.
BitBox: While lesser-known compared to Ledger and Trezor, BitBox wallets focus on simplicity and security. The BitBox02 model offers secure backup solutions and supports multiple cryptocurrencies, making it a viable choice for those seeking an alternative option.
Security Software for Comprehensive Protection
No matter how secure your wallet is, your device is still a potential entry point for attackers. Robust security software can protect against malware, viruses, and other threats that target crypto users.
- Antivirus Solutions: Programs like Norton, Bitdefender, and Kaspersky are equipped with advanced threat detection systems tailored for crypto security.
- Anti-Malware Tools: Malwarebytes is a top choice for detecting and removing malicious software that can compromise your device.
- Firewall Protection: Use a strong firewall to block unauthorized access to your network, especially when accessing crypto wallets and exchanges.
Multi-Factor Authentication (MFA) Solutions
Multi-factor authentication (MFA) adds an extra layer of protection by requiring more than just a password to access your accounts. MFA significantly reduces the risk of unauthorized access, even if your password is compromised.
Authenticator Apps: The First Choice for Enhanced Security
Unlike SMS-based 2FA, which can be intercepted through SIM swap attacks, authenticator apps generate time-based one-time passwords (TOTP) that are far more secure.
- Google Authenticator: A widely used app that provides simple and reliable two-factor authentication. While it lacks cloud backup, it remains a top choice for crypto security.
- Authy: Offers cloud backup and multi-device support, making it a preferred option for users who want extra flexibility. Authy also allows easy recovery of codes if you lose your device.
- Microsoft Authenticator: Provides similar features to Google Authenticator and supports biometric authentication for additional security.
Biometric Security: Adding Another Layer
Where available, biometric security features such as fingerprint scanning and facial recognition are highly recommended. These methods are harder to replicate and add another layer of protection to your devices and accounts.
Educational Platforms and Security Alerts
Staying informed about the latest security threats and best practices is crucial in the fast-moving crypto space. With hackers constantly developing new attack methods, regular updates and education can make all the difference.
Crypto Security News and Alerts
Staying current on security news helps you stay ahead of emerging threats. Trusted platforms provide timely alerts about new attack vectors, vulnerabilities, and industry updates.
- TawkCrypto: Known for its in-depth coverage of crypto security and industry trends, TawkCrypto offers valuable insights and practical security tips.
- CoinDesk: A leading crypto news outlet that regularly publishes reports on hacks, phishing scams, and wallet vulnerabilities. Subscribing to CoinDesk’s security section keeps you updated on major developments.
Community Resources and Forums
Engaging with online crypto communities can provide firsthand accounts of security threats and access to a network of experienced users who can offer advice. However, it’s essential to stick to trusted forums and avoid giving out sensitive information.
- Reddit: Subreddits like r/CryptoCurrency and r/Bitcoin are excellent for staying informed, but always verify any advice independently.
- Discord Channels: Many crypto projects maintain Discord communities where security updates and alerts are shared. Just be cautious about interacting with unknown users in private messages, as scammers are prevalent on these platforms.
Tip: Bookmark reputable educational platforms and security blogs, and consider setting up Google Alerts for key phrases like “crypto phishing scam” or “wallet vulnerability” to stay constantly informed.
What to Do If You Get Hacked:
Discovering that you’ve been hacked can be a terrifying experience, especially if your cryptocurrency holdings or personal information have been compromised. The key to minimizing damage is to act quickly and strategically. Here’s a detailed guide on what to do if you fall victim to a hack.
Immediate Actions: Securing Your Accounts and Containing the Damage
The first and most critical step is to contain the situation by securing your compromised accounts. Time is of the essence—every second counts when mitigating the impact of a hack.
1. Change All Passwords Immediately
As soon as you suspect a breach, change the passwords of all associated accounts, especially those connected to your crypto wallets, email, and any linked social media platforms. Use a password manager to generate strong, unique passwords for each account.
- Prioritize your primary email account, as it often serves as the recovery method for other services.
- If the hack involves your mobile phone, contact your carrier to secure your number and ensure you’re not a victim of a SIM swap attack.
2. Enable Two-Factor Authentication (2FA)
If you haven’t already enabled 2FA on critical accounts, do so immediately. Use an authenticator app like Google Authenticator or Authy, as these are more secure than SMS-based 2FA.
3. Disconnect Third-Party Apps and Revoke Permissions
Hackers often exploit previously granted permissions to access your accounts. Go through the settings of your social media, crypto wallets, and exchanges to revoke access for any suspicious or unused third-party apps.
4. Notify Exchange Platforms
If your crypto assets have been affected, contact your wallet provider and any exchange platforms you use. Inform them of the breach and ask for assistance in freezing transactions or recovering lost funds (if possible). Some exchanges may have protocols in place to help users in these situations.
Report the Incident: Informing Authorities and Relevant Organizations
After taking immediate steps to secure your accounts, it’s essential to document and report the incident. This not only helps in tracking the perpetrators but may also be necessary for insurance claims or legal proceedings.
1. Contact Local Law Enforcement
File a report with your local police or cybercrime division. Provide as much detail as possible, including the nature of the hack, affected accounts, and any financial losses. While recovery might be challenging, reporting the incident creates an official record and may deter further attacks.
2. Notify Cybersecurity Agencies or Watchdogs
In many countries, dedicated cybersecurity agencies can offer advice or investigate hacking incidents. For crypto-related hacks, you can also report the case to relevant blockchain analytics firms that specialize in tracking stolen funds.
3. Inform Your Contacts and Network
If the hack involves your social media accounts, it’s crucial to inform your followers or contacts about the situation. This prevents the hacker from using your account to spread further scams. A simple message explaining the hack and advising others not to click on suspicious links from your account can help contain the damage.
Seek Professional Help: Cybersecurity Experts and Recovery Services
Recovering from a hack is a complex process that may require professional assistance. Engaging experts can help you assess the extent of the damage and ensure your systems are secure.
1. Cybersecurity Consultation
A cybersecurity expert can conduct a comprehensive audit of your digital footprint to identify vulnerabilities. They will help you clean your devices, remove malware, and implement stronger security measures to prevent future incidents.
2. Blockchain Analysis Services
For crypto-specific hacks, blockchain analytics firms can track stolen funds across the blockchain. While recovery is not guaranteed, these firms can help identify where your funds were transferred and alert exchanges to freeze suspicious wallets.
3. Legal and Financial Advice
If significant financial losses are involved, consider consulting a legal professional with experience in cybercrime or digital asset law. They can guide you on potential recovery options and assist with insurance claims if your losses are covered.
Rebuilding and Preventing Future Hacks
Once the immediate crisis is under control, take the time to strengthen your overall security posture. Learn from the incident and implement additional layers of protection to reduce the likelihood of future hacks.
- Audit Your Security Regularly: Review your accounts and devices periodically to ensure no vulnerabilities remain.
- Backup Your Recovery Phrases: Store your wallet recovery phrases and private keys offline in a secure location.
- Stay Informed: Follow reputable security blogs and news outlets to keep up with the latest threats and best practices.
Final Thoughts
Crypto security is an ongoing process that requires vigilance and continuous education. In 2025, with the threat landscape evolving rapidly, taking proactive steps to secure your assets can make all the difference. Remember: staying informed is your best defense.
Stay safe, stay savvy, and keep your crypto secure!
We hope you found these tips helpful. Don’t forget to share your own security tips and experiences with us on our community channels. Until next time, happy and secure trading!







